Ukraine neglected to tell donors they are committing state, federal, and international arms dealing crimes for the sign the shell or rocket donor campaign Ukraine is running. Here’s the details…
UKRAINE DONORS COULD FACE FEDERAL PROSECUTION via George Eliason
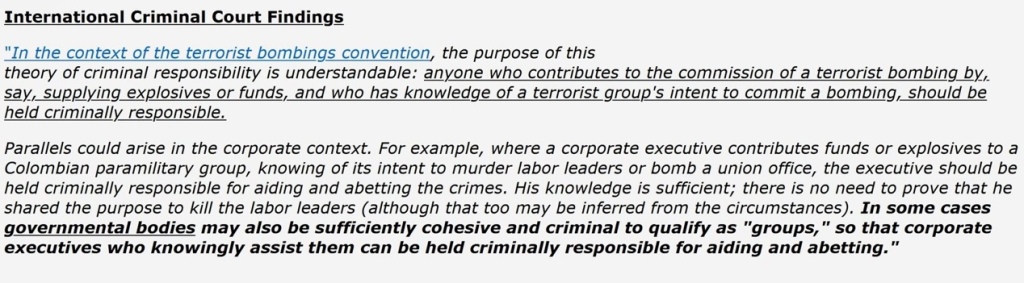


Related:
Crowdfunding a war: How online appeals are bringing weapons to Ukraine
Americans are paying for slogans on bombs aimed at Russians
Ukraine Buys Military Gear With Donated Cryptocurrencies
Ukrainian Hackers Raised Almost $600,000 “for the Armed Forces of Ukraine”
[2015] EuroMaidan| One Year Later- Crowd Funding Donbass Genocide
Treading on a dangerous ground: a conclusion
In the Ukraine-Russia war, civilian cyber volunteers have become the most vocal actors on the cyber front, partially because hacktivism is innately loud and partially because whatever happens on a state-to- state level, where the stakes are considerably higher is stealthy and silent. However, it seems like the Ukrainian IT Army, which is more strategic and precautious in its operations and the various hacktivist groups seem to be treading the thin lines drawn by international law. They make the most of information leaks, data sharing and web defacements, maximise the effects of temporary disruptions and quotidian nuisance without becoming irrevocably involved in the armed conflict. The instances that seem the closest to qualifying as direct participation have been committed against Belarus, a state that despite its obvious leanings is not (yet) at war. The attacks directed at various Russian government websites and information systems or that have interfered with news and broadcasting services will, unless they somehow directly contribute to military harm, leave the perpetrators’ civilian immunity intact. Be it due to mere luck or skilful deliberation, the lack of serious casualties or legal consequences cannot be taken for granted, particularly when considering Russia’s apparently liberal use of the term ‘act of war’ and the swift changes in Russian criminal law.
To avoid the conflict spilling over because of a hack gone wrong, before signing up for any activity inspired by the desire to help a state that has fallen victim to an unjustifiable invasion, an individual should bear in mind their position in relation to any state organ and that of the particular hacktivist group they plan to join. The most important factor that decides the legality and overall safety is still the character of the activity; while information
leaks and anti-propaganda hacks do not turn a civilian into a lawful or unlawful combatant, they do jeopardise ongoing government intelligence operations. On the contrary, hacktivist operations of potentially uncontrollable or indiscriminate effects such as open-source supply chain attacks or anything targeting critical infrastructure are never worth the risks – military, humanitarian or criminal – that they pose.
Cyber vigilantism in support of Ukraine: a legal analysis
Previously:
‘Sign my Rocket’ – the underground crowdfunding industry behind Ukrainian Nazi armed groups

You must be logged in to post a comment.